Category: Cybersecurity
-

Cybersecurity 2026
WEF Global Cybersecurity Outlook 2026
-
SMART-Phones potential
Brief investigation on combined computing power and risks. 1. Global combined capacity of all smartphones 2. Tools to use/control smartphones for grid-computing 3. Smartphone security, forensic via MVT (picture generated by FOTOR (AI) ) Set-up: MVT install (forensic) Grid Computing Wikipedia index (pending decision on Infra) BOINC Github BOINC Alternatives FieldGenius HW: Several Android Smart-phones/…
-

Drone shield
Trial set-up: Drone approach alert, take control or RF disruption. HW: DJI mini 2, HackRF One, Pixel 7, … SW references: Drone shield commercial; military Drone jamming or spoofing is ilegal, only reviewed for study purpose in relation to defend company/private property under illegal recognition activity via drone. . Legal issues with counter drone tech…
-

Data breach 2022
Verizon Report IBM Report HAI Report
-
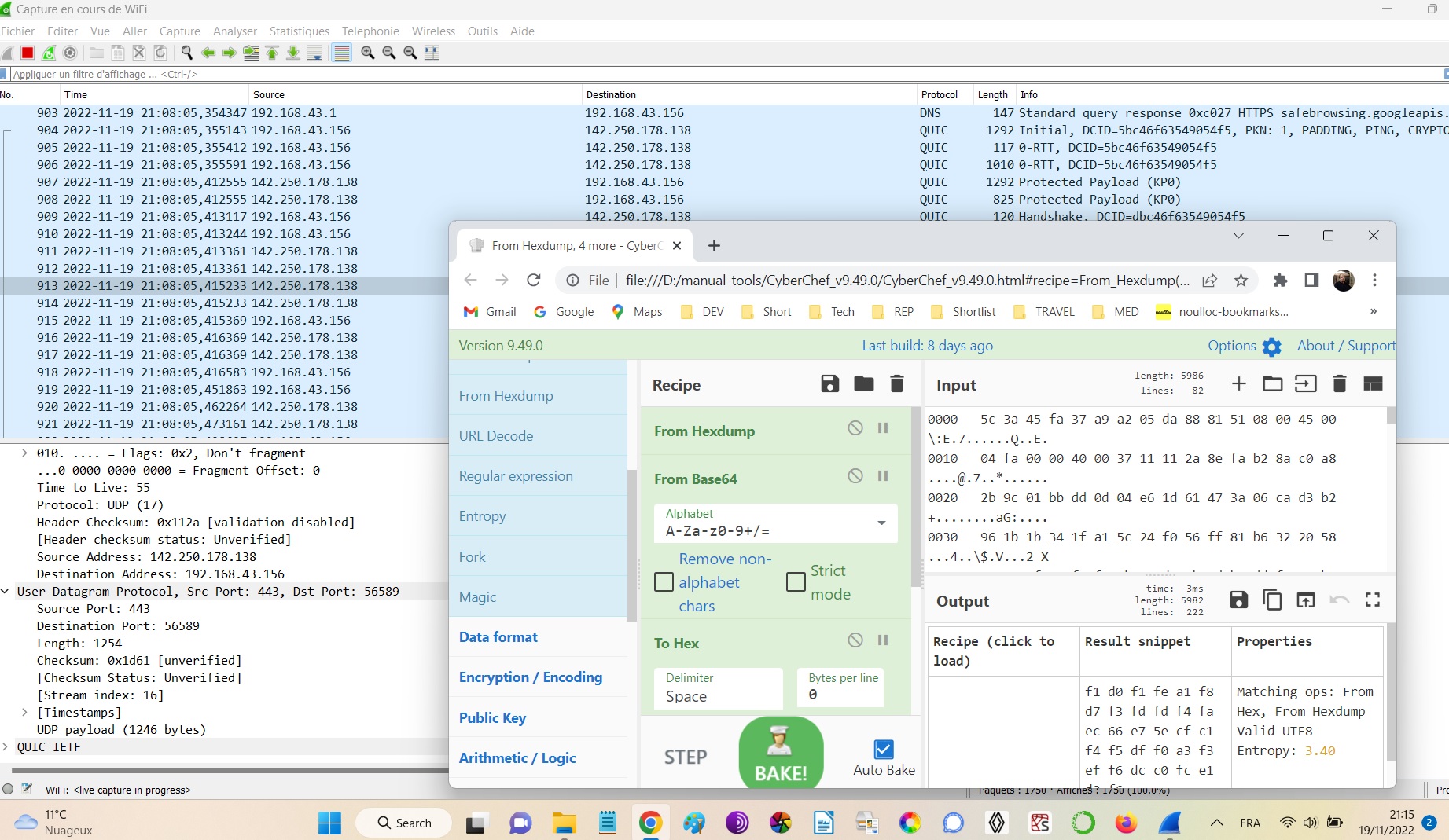
Wireshark & CyberChef
Easy setup. Investigate Wifi local area and hotspot traffic (e.g. honeypot hotspot). Wireshark traffic logs, filter, decrypt. To perform whitehat pentests.
-
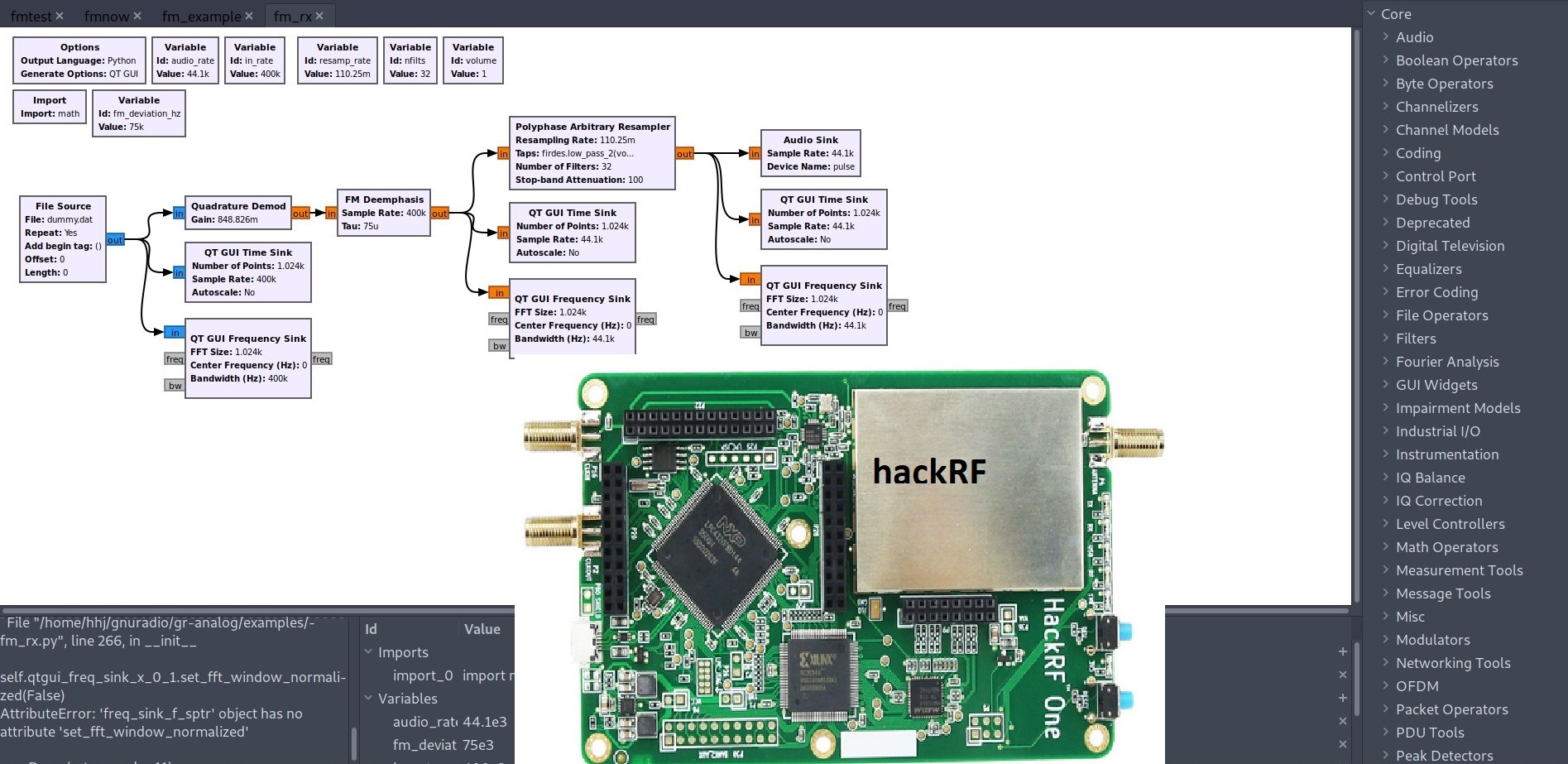
IoT pentest via hackRF and Gnuradio
Set-up end-to-end is complex (here in Parrot Security OS and generic hackRF HW) Recon and Pentest of the growing number of connected devices many with weak security (Car, house radio-keys, RF tags etc.). Basic home or biz pentest: List critical devices and frequency ranges, activate/trigger device and record for post-processing. Security may be OK or…
-
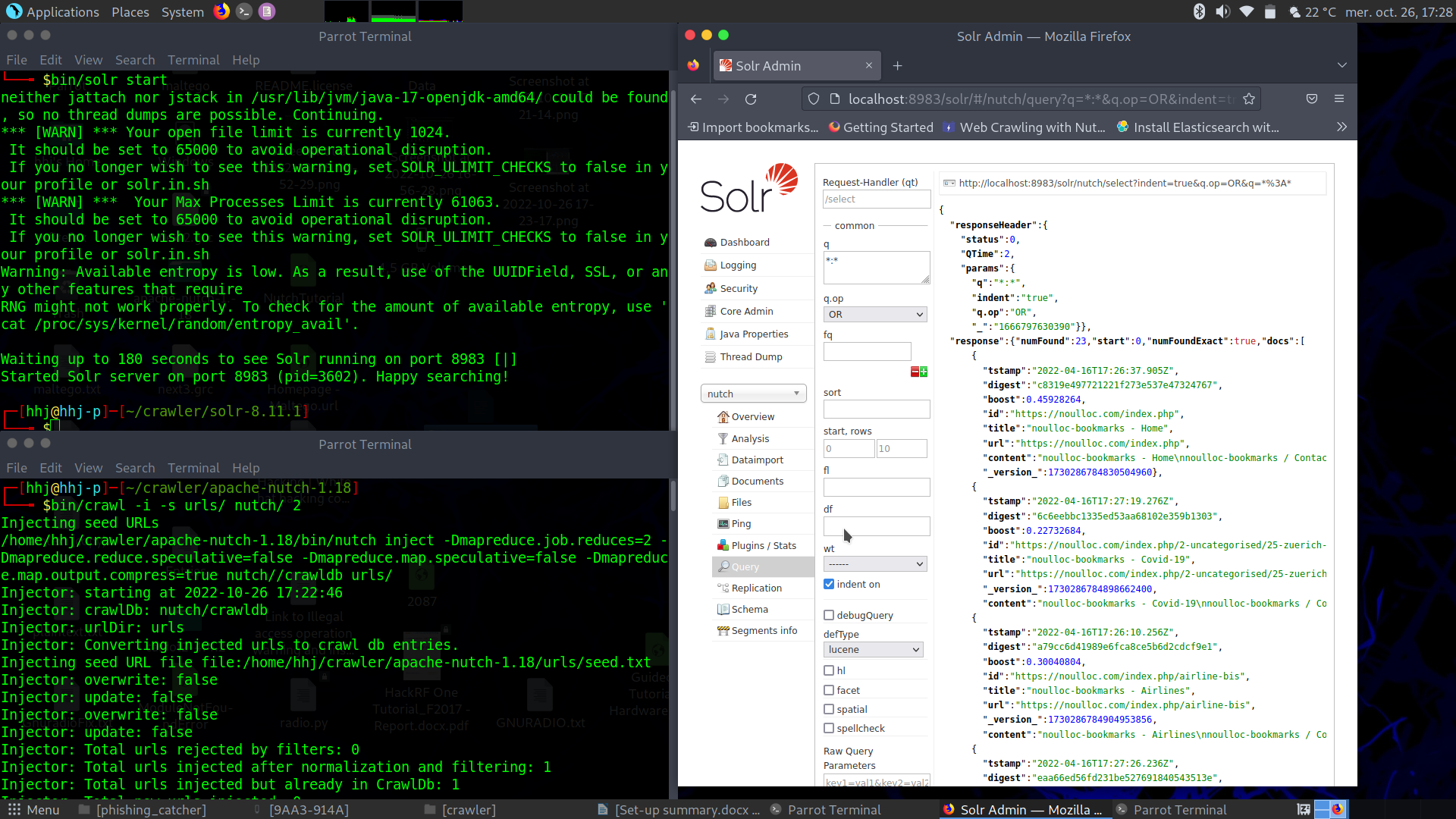
Recon Solr (DB) Nutch (spider)
Set-up medium+ complex (here in Parrot Security OS – Debian Linux distribution). Allows for crawl list of URL’s on flexible depth level with sophisticated keywords, generating crawl results in the Solr DB for subsequent analysis, analytics or export to graphic tools. Publish in dynamic Web site. Nutch tutorial https://www.digitalocean.com/community/tutorials/how-to-install-java-with-apt-get-on-debian-8
-
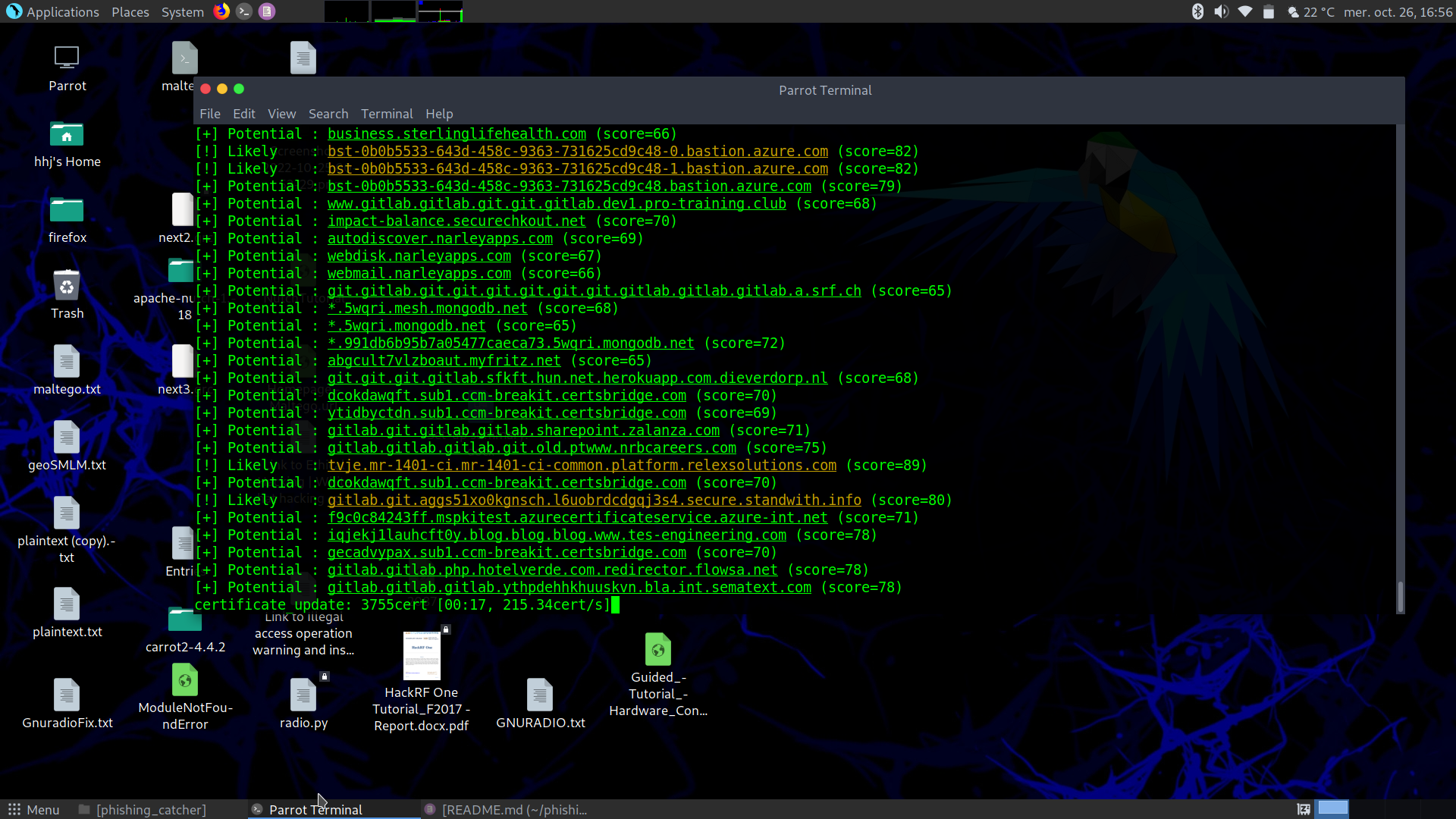
Phishing-catcher
Business can anticipate coming phishing attacks via regular run of the .py script scanning with keyword (e.g. company URL string) new certificat registrations. Then block in firewall and mailing systems. Easy set-up, here in Parrot Security OS (Debian Linux distribution) Source download source and run: pip install -r requirements.txtconfigure/edit: suspicious.yaml and external.yamlrun via: ./catch_phishing.py Seems…
-
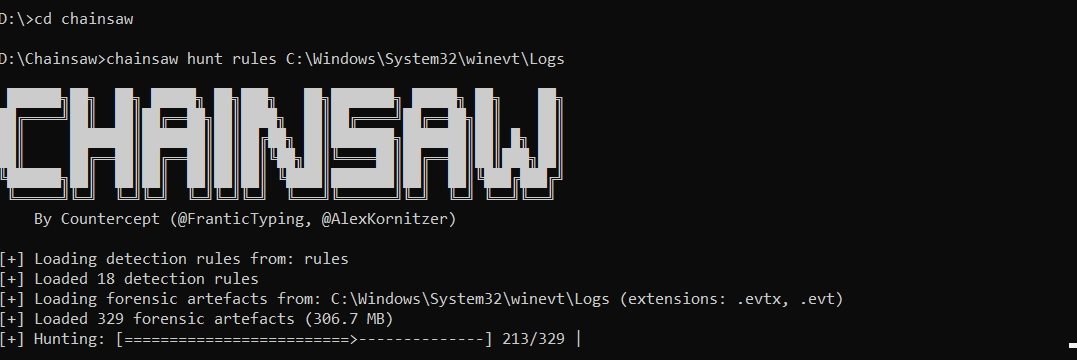
Chainsaw
Fast primary check if your Windows OS based device is compromised, hacked. Automated (event) log search. Define search string (error) based on threat information or define pattern in rules directory. Easy set-up in Windows OS Github source Sample after install: chainsaw hunt rules C:\Windows\System32\winevt\Logs chainsaw search error C:\Windows\System32\winevt\Logs chainsaw search < Audit Failure > -i…