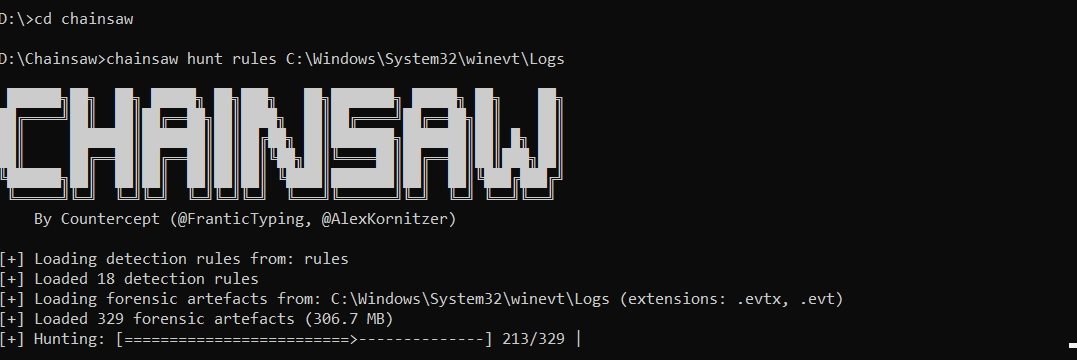
Fast primary check if your Windows OS based device is compromised, hacked. Automated (event) log search. Define search string (error) based on threat information or define pattern in rules directory.
Easy set-up in Windows OS
Sample after install:
chainsaw hunt rules C:\Windows\System32\winevt\Logs
chainsaw search error C:\Windows\System32\winevt\Logs
chainsaw search < Audit Failure > -i C:\Windows\System32\winevt\Logs
More interactive log search and investigation also via Cyberchef, ISC example (by Didier Stevens)